WordPress has made the web designers’ lives easier. It has reduced the web development time & cost drastically. The CMS is so powerful that more and more people are converting/migrating their sites to WordPress. With ease comes the danger of being compromised. If compromised – your site will not function properly. It may leak your confidential information, give access to spammers and use your hosting account for spamming, give access to hackers who may upload files to run phishing attack.
Let us first know why a wordpress website gets hacked – gets infected to malware.
WordPress website becomes vulnerable due to the following reasons:
1. WordPress is not updated
2. Plugins are not updated
3. The administrator username passwords are too easy.
4. The computer used to administer the wordpress site (Admin area & cPanel/FTP) is itself infected to viruses.
5. Use of nulled / pirated templates or Plugins – in which codes are embedded which gives the hacker the access.
6. Presence of other hacked script/website in the same hosting account.
7. Unsecured Web hosting. (Poorly configured server, easy guessable passwords etc).
How to identify your WordPress website is hacked or have malware in it?
The website will start behaving abnormally. The website may go blank, break or become very slow. The hackers may get access of your web hosting account and may upload their own scripts and start spamming or create phishing pages. Your web hosting account will be exhausted and your hosting company may suspend your account for resource over usage and spamming. These are some of the symptoms your WordPress is being hacked. If you dig deeper and want to be sure – you need to check the files of your WordPress system. You may find unknown folders (Directories) and files. That’s not it!! Many of the php files (Mostly theme & Plugin files) may contain malicious code in those.
How to clean the WordPress website:
1. First and most important step is – make your computer / work station secured. This includes – having a very good antivirus / Internet security system. Get one (Kaspersky, Bitdefender, AVG, Norton … bla bla bla) if you do not have it yet. Make a full system scan and get rid of any threats (viruses, Trojans).
2. Download the WordPress website in your computer (using FTP or Control panel File Manager). To reduce the time – you may Zip (compress) the full site if you have a control panel in your hosting and if it allows compressing.
3. Extract the folder – if you’ve downloaded a zip copy. Keep the zip file as backup and do not delete it – so that you can use it if anything goes wrong when you try to fix the site. Take a backup of your database too. Now, go into the extracted WordPress folder.
4. The next part is cleaning the malicious code. This is a bit tricky part. There may be hundreds of hundreds of files which may contain malicious code (hacker embedded code). Mostly the php files in the Themes and plugins get infected. But php files in other directories may get infected to. I will show you a trick which will help you get rid of these codes within few seconds.
a. You’ll need Adobe’s Dreamweaver tool or something with similar features. You can download Adobe Dreamweaver Trial from this link.
b. Now you need to find a file which contains malicious code. Go to the active theme folder under “wp-content” >> “Themes”.. Then open the index.php file using Dreamweaver. The malicious code should be either at top or at the bottom and should look like this:

All the infected files should contain the same code. If you carefully look in the picture above you’ll notice that the malicious code starts and ends with “//###==###”. The code can vary from what you see in the above picture – but it will be something like this. You’ll need to remove this chunk of code from all the files.
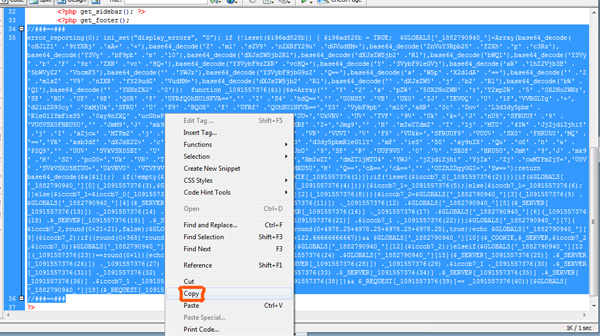
c. You have to use the Find & Replace function in Dreamweaver. Copy the malicious code (starts and ends with “//###==###” in this case). Now press “CTRL + F” and the Find & Replace option should appear.
d. Paste the malicious code in the “Find” box and keep the “Replace:” Box empty. Now you have to choose “Folder..” option from the drop down menu “Find in” and “Source Code” option from the drop down menu “Search:”.
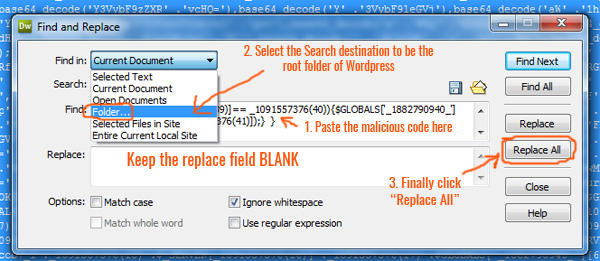
Now you have to choose the search Destination Folder:
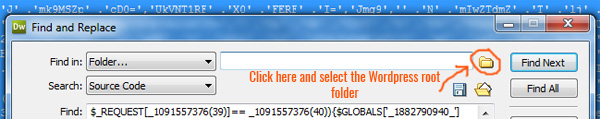
Choose the root directory of wordpress site from your local machine. Now press the “Replace All” as shown in the “Find and Replace malicious code with empty box” image. This will wipe off the malicious code from all the files. Now you need to save all the files from “File”>> “Save All” option. You are done with Malicious code removal!! Congrats…
5. The next step is cleaning all the hacker uploaded folders. Your basic wordpress website should have 3 folders in the root folder. wp-admin, wp-content and wp-inlcude. You might have a look at other folders in the root directory and consider removing those if you are sure those doesn’t belong to your website. You can replace all the files and folders from a fresh copy of WordPress except the wp-content folder and wp-config.php files. Remember, If at any stage the website breaks – you have the zip file (mentioned in step 3) as backup.
6. Now you’ll have to prepare your hosting account for re-uploading the cleaned website.
a. The first thing you need to do is – delete all the files of your wordpress site from your hosting account.
b. Change the password of your hosting accounts and change the password of any other FTP accounts in that hosting account.
c. Upload the cleaned WordPress files.
7. After re-uploading the site if it runs properly do the following:
a. Update the wordpress to the latest version.
b. Remove any unnecessary plugin. If you are unsure about which ones are unused – you may skip this step.
c. Update all the plugins & Templates.
d. Change WordPress username and password to a complex one. Do not keep “admin” your username.
8. You need install some third party plugin to harden the site security. For example, you may consider installing ALL IN ONE WP SECURITY & FIREWALL. It will require me to write another similar post to describe the features and performance of this plugin – For now, let me assure you that this is one plugin which will make your website very secure.
It will show you, protect your site and will keep your sites and plugins updated automatically. It can also change the admin directory of your wordpress site changing the admin login link– which will reduce the Admin login attack in your site. There may be other similar plugins with same functionalities. You need to implement this kind of plugins to make and keep your site secured.
9. Take help from professional WordPress malware solution provider: You can take help from professionals who provide WordPress malware removal solutions. WPMalwares is such a provider. These guys are wordpress security specialists and can solve your problem at a very low price. You can save your time for something more important and leave your headache to these guys. They will fix your site and will provide you free support for one year. Moreover, they will add extra layers of security on your website.
For details – please visit: WordPress Malware removal
Feel free to comment if you think I have missed any point or if there are better ways to clean and protect wordpress websites. I will include your suggestions in the main post with your name and link.
wp-goodluck!! 🙂


Thank you. I followed these steps and was able to get my infected site back up, cleaned and running! I appreciate your help.