To redirect all www traffic to non-www URL - you need to add the following lines in .htaccess file: RewriteEngine On RewriteCond %{HTTP_HOST} ^www.example.com [NC] RewriteRule ^(.*)$ http://example.com/$1 [L,R=301] Replace example.com with your own domain name.
Continue readingTag: linux
How to create Raid1 mirroring with 3rd & 4th Drives in OVH servers
OVH panel offers easy Raid configuration for the partitions in up to 2 drives. Recently I was working on a server that has 2 SSDs and 2 HDDs. The server is intended to serve as a Shared Hosting server. My idea was to install the OS on the SSDs and use the HDDs for hosting…
Continue readingHow to clean /tmp directory automatically in Linux/cPanel using tmpwatch
The “tmpwatch ” command in linux is to removes files which haven't been accessed for a period of time. The tmpwatch recursively removes files which haven't been accessed for a given time. Normally, it's used to clean up directories which are used for temporary holding space such as /tmp. If you are noticing "/tmp" getting…
Continue readingHow to recursively change Directory & File permission to 755 & 644 respectively
To change all the directories to 755 (drwxr-xr-x): find /directory_location -type d -exec chmod 755 {} \; To change all the files to 644 (-rw-r- -r- -): find /directory_location -type f -exec chmod 644 {} \;
Continue readingWhitelist IP or IP range in/out using iptables
#Flush existing rules iptables -F # Set up default DROP rule for eth0 (Assuming eth0 is the Ethernet Port) iptables -P INPUT DROP # Allow existing connections to continue iptables -A INPUT -i eth0 -m state --state ESTABLISHED,RELATED -j ACCEPT # Accept everything from the 192.168.0.x network iptables -A INPUT -i eth0 -s 192.168.0.0/24 -j…
Continue readingHow to change default SSH port 22 to something else
Internet connected Linux servers are always vulnerable to exploitation by the hackers/intruders. One of their common attack is through SSH. By default SSH servers are configured to listen to port 22 for SSH connection. Changing the port to something else will definitely add an additional measure in securing the server. How to Change Default SSH…
Continue readingHow to Clear bash / SSH / Terminal command history in Linux
You might need to wipe off the command history that you've executed in your linux system for various reason. Normally when logged into the bash / SSH terminal - if the Up Arrow key is pressed - previously executed commands are shown. To completely delete the history type the following command: # history -c #…
Continue readingHow to find the IP addresses of a Linux system
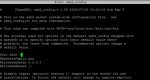
The following command in a linux based system will show all the IPs assigned to that system: # ip addr show Or alternatively, if you'd like to know the IP address(es) of a certain port (for example eth0) type the following: # ip addr show eth0 Sample output: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state…
Continue readingDetermine if the storage is SSD or HDD – using linux command
You've purchased a Cloud server or a Virtual server. The server provider says it comes with an SSD (Solid State Drive). Now you definitely would like to verify whether the storage is indeed SSD or is it simple HDD (Hard Disk Drive). If you're server is running on any version of Linux OS (kernel version…
Continue readingGHOST vulnerability in Linux distributions and its Solution
A GNU C Library (glibc) vulnerability - termed as "GHOST Vulnerability" was announced to general public on 27 January 2015 - after a Cloud research company Qualys discovered this major security vulnerability. This vulnerability enables hackers to remotely take control of systems without even knowing any system IDs or passwords. How to Quickly Identify if your…
Continue reading