I recently suffered by a worm named W32/Mysamurai. It changed the background of the C:\WINDOWS folder with a scary photo.
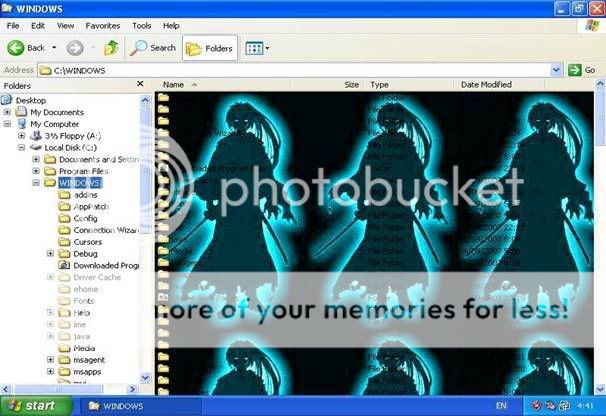
My pc was dead slow and I was looking for the solution. Atlast the Norton Security Scan in my PC could detect it. There was a file named windxp.ini in the C:\WINDOWS\System32 folder which was responsible for that. As soon as Norton Security scan detected it, I deleted it and I found my C:\WINDOWS folder back to how it should Look. Mcafee Security Center couldn’t detect it and neither could it remove it.
Information about the W32/Mysamurai Worm:
W32/Mysamurai is a worm. The worm will infect Windows systems and spreads through shared network drives.
Upon execution, the worm copies itself as:
(Temp name).tmp in the Windows Temp folder,
AdobeGama.pif in the Documents and Settings\All Users\Start Menu\Programs\Startup folder,
AdobeGama.pif in the %User Profile%\Start Menu\Programs\Startup folder,
htSystem.cfg in the C:\System Volume Information\_Resto~1 folder,
explore.exe in the Windows folder.
It also copies iteslf as the following files in the Windows System folder.
CommandPrompt.Sysm
NvMedia.sysm
Restoration.msd
Windows 3D.scr
odbcad32.dll
shareNet.msd
Ngsys.exe
runer.exe
rvshost.exe
system31.exe
userint.exe
windxp.exe
winzipt.exe
It also creates WindXP.ini file in the Windows System folder.
The worm modifies the Desktop.ini configuration information file present in the Windows and Windows System folder.
It modifies the registry at the following location to ensure its automatic execution at every Windows startup:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_CURRENT_USER\Control Panel\Desktop
HKEY_CLASSES_ROOT\.Msd
HKEY_CLASSES_ROOT\.Msd\DefaultIcon
HKEY_CLASSES_ROOT\.Msd\Shell\Open\Command
HKEY_CLASSES_ROOT\.sysm
HKEY_CLASSES_ROOT\.sysm\DefaultIcon
HKEY_CLASSES_ROOT\.sysm\Shell\Open\Command
It also modifies the registry to ensure that the screensaver is active and will run. The threat will run when the computer is restarted in Safe Mode, and that file extensions are not shown.
The worm then spreads by copying itself to shared drives.
This worm first appeared on September 02, 2007.
Blueball Other names of W32/Mysamurai Worm:
This Worm is also known as W32.Mysamurai.
